The Eclipse moquitto provides the open source message Broker which supports the Mqtt Protocol versions 5.0,3.11,3,1.The Mqtt protocol is a very lightweight and can be operated on microcontroller based systems like Raspberry Pi to computer PC servers. The Mqtt clients can be operated from the small microcontroller based sensor which are constrained.
The Mosquitto Brokers can be installed on your systems by visiting the Eclipse mosquitto Download page.Here the setup file suitable to various os can be downloaded and installed. IF want to How to setup the Mosquiito Broker on WIndows PC then click here.
In this article, we are going to see how to use SSL\TLS with Mosqutto Broker or secure mosquitto Broker.With we ensure secure or encrypted communication wtth Mqtt communication with the Mosquitto Broker.We will be OpenSSL utility to generate the CA key,CA certificates,Server key and Server certificate. We are using Ubuntu 20.04 based system here.
SSL(Secure Sockets Layer) and TLS(Transport Layer) are protocols for implementing secure or encrypted link over LAN or WAN networks .OpenSSL provides the software utility for full featured cryptography and secure communication.
In order to install OpenSSL on Ubuntu based systems, run the following command from the terminal of the Ubuntu os.
sudo apt-get install openssl
After successful installation of openssl ,follow the steps as given below for generations of CA keys, CA certificates, Server keys and Server Certificates,
1. Create a CA key for client
openssl genrsa -des3 -out ca.key 2048
This command generates ca.key having CA keys for the clients.
2. Create CA certificate using the CA key
openssl req -new -x509 -days 1833 -key ca.key -out ca.crt
This command generates the CA certificates for the client.
3. Create a broker key wout encryption
openssl genrsa -out server.key 2048
This command generates keys for Broker which can be used to .csr file.
4. Request for Broker certificate.Create .csr file with broker key
openssl req -new -out server.csr -key server.key
This command geberates request for Broker cerificate i.e. .csr file
5 Create a broker certificate
openssl x509 -req -in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out server.crt -days 360
This command generates server certificate which is valid fro 360 days.
Before executing these command, create one folder(certs) to save the certificates and key files.
Run the terminal from this folder.
Step 1: Generate key file for the client
Generate keys for the clients by executing this command. As a result ca.key file will be generated.
openssl genrsa -des3 -out ca.key 2048
Run this command from the terminal.
The system will prompt to enter and reenter password. I entered 1234 as password for the ca.key file.
Step 2: Generate CA certificate file
Generate CA certificate file using ca.key file for the client by running the following command from the terminal.
As a result, ca.crt file will be generated. Here the ca.key file is required.
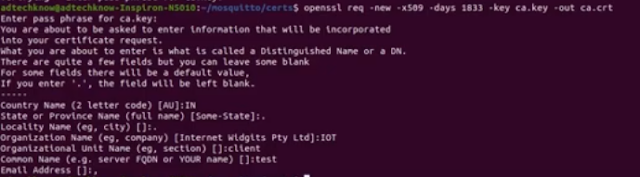
openssl req -new -x509 -days 1833 -key ca.key -out ca.crt
The system asks for the password for ca.key file. Enter the password. You can do the similar entries to provide the information asked for. In order to leave the entry blank enter . and the press enter.
Step 3:Generate Keys for Server or Broker without encryption
The keys for server or Broker are generated by running the command from the terminal. As a result,the server.key file is generated.
openssl genrsa -out server.key 2048
Step 4: Request for Broker certificate or generate .csr file with server keys
The request for Broker certificate can be made by using the following command. As a result, ,server.csr file is generated.
openssl req -new -out server.csr -key server.key
You can provide the information as shown in the image or you can enter different info as required. Please enter the Common name as your PC ip or PC name. I have entered Ip of my pc as shown in the image. The information regarding exstra attribute is not privided as we signing the certificate on our own.